
Hippocrates’ fundamental principle is a stable component of our present day security paradigm. The principle is to only divulge information as necessary to benefit the patient.
Security of PHI (electronic or paper) is more than simply HIPAA regulations. Security in the larger sense involves access and authorization controls, accessibility guidelines, hardware and software security structures, physical security standards and practices, system firewall security, physical identification and management of PHI transported out of a facility, in addition to other requirements involving locking doors, area access restrictions, access to communication lines/wires and servers, and disaster preparedness and recovery. The subsections listed below are some of the major components of security related to e-PHI and paper PHI in a general sense.
http://www.cms.hhs.gov/SecurityStandard/Downloads/SecurityGuidanceforRemoteUseFinal122806.pdf
Accessibility - See HIPAA Physical and Technical requirements below
Paper vs. Electronic storage - A day in the life of a medical record.
Electronic systems offer a quantum leap in the beneficial uses of medical records, by allowing the full value of all information ever written down or stored as images to be indexed and utilized by multiple caregivers in multiple locations at any time.This report compares the observations of a paper-based records environment with an electronic-based records environment. It discusses "what the public can use to make a reasoned comparison between current and emerging approaches to medical record security".
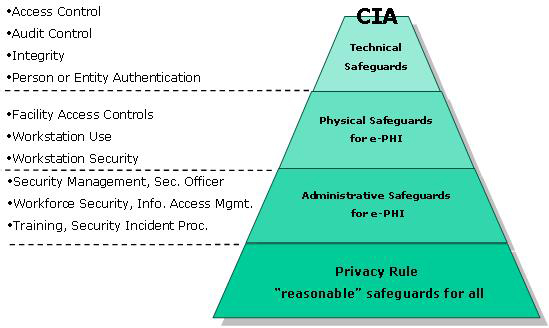
Hardware and Software Security: CIA = Confidentiality, Integrity, Availabiltiy


http://www.hipaaacademy.net/consulting/hipaaSecurityRuleOverview.html
Disaster Recovery: As in the paper environment, the advent of EHRs cause every organization to consider what would happen in the event of a disaster. How long can the system be down? What are the vital applications that must be brought back first? Should our disaster recovery plan include offsite back-up of data? If so, how often should the files be backed-up? A disaster can happen any day at any time and can include: flood, explosion, computer malfunction, accident, grievious act... Being prepared for any event is not something that can be left to consideration after the fact. Disaster preparedness and recovery planning must be a pro-active priority - we have only to think of the impact Katrina had to learn our observational lesson.
HIMSS - Privacy and Security Toolkit
The Sound Security Practices document identifies resources such as standards and guidelines that are well established. The security practices are grouped under three major categories namely, standards organizations, government agencies and others such as trade associations, think tanks, security practitioners, etc.
Guidelines for Managing Information Security Programs at Organizations Using Computer-based Patient Record Systems - This document provides information security guidelines to assist organizations implementing computer-based patient record systems to establish formal information security programs
Privacy and Security Questionnaire - a self-assessment tool that will allow healthcare provider organizations or other product purchasers to assess the core security controls inherent within an application or system that will process or store ePHI.
In the past, healthcare organizations have used multiple identification formats when conducting business with each other – a confusing, error-prone and costly approach. It is expected that standard identifiers will reduce these problems. The Employer Identifer Standard, published in 2002, adopts an employer's tax ID number or employer identification number (EIN) as the standard for electronic transactions. The NPI, published in 2004, requires hospitals, doctors, nursing homes, and other healthcare providers to obtain a unique identifier when filing electronic claims with public and private insurance programs. Providers can apply for an identifier once and keep it if they relocate or change specialties. A final standard for a Health Plan identifier has not yet been published.
The final Security Rule was published on February 20, 2003 and provides for a uniform level of protection of all health information that is housed or transmitted electronically and that pertains to an individual. The Security Rule requires covered entities to ensure the confidentiality, integrity, and availability of all electronic protected health information (ePHI) the covered entity creates, receives, maintains, or transmits. It also requires entities to protect against any reasonably anticipated threats or hazards to the security or integrity of ePHI, protect against any reasonably anticipated uses or disclosures of such information that are not permitted or required by the Privacy Rule, and ensure compliance by their workforce. Required safeguards include application of appropriate policies and procedures, safeguarding physical access to ePHI, and ensuring that technical security measures are in place to protect networks, computers and other electronic devices. The Security Standard is intended to be scalable; in other words, it does not require specific technologies to be used. Covered entities may elect solutions that are appropriate to their operations, as long as the selected solutions are supported by a thorough security assessment and risk analysis.
Physical safeguards are physical measures, policies, and procedures to protect a covered entity’s electronic information systems and related buildings and equipment, from natural and environmental hazards, and unauthorized intrusion. Figure 4 summarizes the Physical Safeguards’ standards and their associated required and addressable implementation specifications.
Standards | Implementation Specifications | R = Required A = Addressable |
| Facility Access Controls | Contingency Operations | A |
| Facility Security Plan | A | |
| Access Control and Validation Procedures | A | |
| Maintenance Records | A | |
| Workstation Use | R | |
| Workstation Security | R | |
| Device and Media Controls | Disposal | R |
| Media Re-use | R | |
| Accountability | A | |
| Data Backup and Storage | A |
Technical safeguards refer to the technology and the policy and procedures for its use that protect electronic PHI and control access to it. Figure 5 summarizes the Technical Safeguards’ standards and their associated required and addressable implementation specifications.
Standards | Implementation Specifications | R = Required A = Addressable |
| Access Control | Unique User Identification | R |
| Emergency Access Procedure | R | |
| Automatic Logoff | A | |
| Encryption and Decryption | A | |
| Audit Controls | R | |
| Integrity | Mechanism to Authenticate Electronic PHI | A |
| Person or Entity Authentication | R | |
| Transmission Security | Integrity Controls | A |
| Encryption | A |
http://www.microsoft.com/mscorp/twc/default.mspx
News Links:
http://www.technewsworld.com/perl/section/security/
http://aspe.hhs.gov/admnsimp/bannerps.htm
http://www.hhs.gov/ocr/combinedregtext.pdf
General Information:
HIMSS - Privacy and Security Toolkit http://www.himss.org/asp/privacySecurityTree.asp?faid=78&tid=4