CPS@Duke: Synthesis of Platform-Aware Attack-Resilient Control Systems
Menu:
News:
April 2014:
Our paper wins the Best Paper Award at ICCPS'2014!
January 2014:
Paper on robustness of attack-resilient state estimators accepted at ICCPS'2014, part of the CPSWeek!
December 2013:
Paper on resilient history-based sensor fusion accepted at HICONS'2014, part of the CPSWeek!
November 2013:
Paper on attack resilient sensor fusion accepted at DATE'14!
September 2013:
Miroslav Pajic is a program committee member at HiCoNS!
July 2013:
Paper accepted at CDC'13!
July 2013:
LandShark demonstration at the HACMS review
Project Overview:
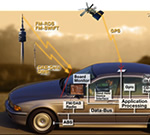
Modern embedded control architectures have moved from isolated closed-loop control systems to open architectures, such as new automotive architectures with services that include remote diagnostics, code updates, and vehicle-to-vehicle communication. However, this shift has also introduced security vulnerabilities that are easily exploitable, since the current embedded systems have not been built with security in mind. An illustrative example are the recently exposed security vulnerabilities in present-day vehicles, which can be simply exploited by an attacker to disrupt the operation of a car by either disabling the vehicle or hijack it, giving the attacker the ability to control it instead.
The challenge of designing secure embedded-control systems has to be addressed on two levels. First, it is necessary to design attack resilient control schemes and architectures, capable of dealing with attacks on the environment of the controller, including attacks on sensors, actuators, and communication media. To utilize the knowledge of the system dynamics for attack detection and identification, we have to focus on new problems, such as sensor and controller fusion under attacks, detecting system attacks in the presence of noise and model uncertainty, and resilient control of nonlinear systems. On the other level, it is essential to ensure that the code generated for the resilient controller correctly implements the desired algorithm while preventing injection of malicious code into the controller itself. This can be achieved by providing a set of control and security code invariants that can be verified under a certain set of assumptions on the underlying computation/communication platform. In this case, the main challenges are in defining a suitable set of control invariants, along with formalisms that can be used to capture the platform assumptions.
Papers:
-
Miroslav Pajic, Insup Lee, and George J. Pappas, "Attack-Resilient State Estimation for Noisy Dynamical Systems", IEEE Transactions on Control of Network Systems, accepted.
-
Miroslav Pajic, James Weimer, Nicola Bezzo, Oleg Sokolsky, George J. Pappas, and Insup Lee "Design and Implementation of Attack-Resilient Cyber-Physical Systems", IEEE Control Systems, to appear.
-
Fei Miao, Quanyan Zhu, Miroslav Pajic, and George J. Pappas, "Coding Schemes for Securing Cyber-Physical Systems Against Stealthy Data Injection Attacks", IEEE Transactions on Control of Network Systems, to appear.
-
Radoslav Ivanov, Miroslav Pajic, and Insup Lee, "Attack-Resilient Sensor Fusion for Safety-Critical Cyber-Physical Systems", ACM Transactions on Embedded Computing Systems, 2016.
-
Junkil Park, Miroslav Pajic, Insup Lee, and Oleg Sokolsky, "Scalable Verification of Linear Controller Software", Tools and Algorithms for the Construction and Analysis of Systems (TACAS), 2016.
-
Radoslav Ivanov, Miroslav Pajic, and Insup Lee, "Attack-Resilient Sensor Fusion for CPS", Multisensor Data Fusion: From Algorithm and Architecture Design to Applications, CRC Press, 2015.
-
Miroslav Pajic, Paulo Tabuada, Insup Lee, and George J. Pappas, "Attack-Resilient State Estimation in the Presence of Noise", 54rd IEEE Conference on Decision and Control (CDC), Osaka, Japan, 2015.
-
Miroslav Pajic, Junkil Park, Insup Lee, George J. Pappas, and Oleg Sokolsky, "Automatic Verification of Linear Controller Software", ACM SIGBED International Conference on Embedded Software (EMSOFT), Amsterdam, Netherlands, 2015.
-
Mohammad Al Faruque, Francesco Regazzoni, and Miroslav Pajic, "Design Methodologies for Securing Cyber-Physical Systems", International Conference on Hardware/Software Codesign and System Synthesis (CODES+ISSS), Amsterdam, Netherlands, 2015..
-
Radoslav Ivanov, Nikolay Atanasov, Miroslav Pajic, George J. Pappas, and Insup Lee, Robust Estimation Using Context-Aware Filtering", 53rd Annual Allerton Conference on Communication, Control, and Computing (Allerton), 2015.
-
Radoslav Ivanov, Nikolay Atanasov, Miroslav Pajic, Insup Lee, and George J. Pappas, Robust Localization Using Context-Aware Filtering", Workshop on Multi VIew Geometry in Robotics, in conjunction with RSS (MVIGRO), Rome, Italy, 2015.
-
Junkil Park, Radoslav Ivanov, James Weimer, Miroslav Pajic, and Insup Lee, "Sensor Attack Detection in the Presence of Transient Faults", 6th ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Seattle, WA, 2015.
-
Miroslav Pajic, James Weimer, Nicola Bezzo, Paulo Tabuada, Oleg Sokolsky, Insup Lee, and George J. Pappas, "Robustness of Attack-resilient State Estimators", 5th ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Berlin, Germany 2014. (Best Paper Award).
-
Radoslav Ivanov, Miroslav Pajic, and Insup Lee, "Resilient Multidimensional Sensor Fusion using Measurement History", 3rd ACM International Conference on High Confidence Networked Systems (HiCoNS), Berlin, Germany 2014.
-
Radoslav Ivanov, Miroslav Pajic, and Insup Lee, "Attack-Resilient Sensor Fusion", Design, Automation and Test in Europe (DATE), Dresden, Germany 2014.
-
Fei Miao, Quanyan Zhu, Miroslav Pajic, and George J. Pappas, "Coding Sensor Outputs for Injection Attacks Detection", 53rd IEEE Conference on Decision and Control (CDC), Los Angeles, CA 2014.
-
Oleg Sokolsky, Miroslav Pajic, Nicola Bezzo, and Insup Lee, "Architecture-Centric Software Development for Cyber-Physical Systems", Workshop on Cyber-Physical System Architectures and Design Methodologies at ESWeek (CPSArch), New Delhi, India 2014.
-
James Weimer, Nicola Bezzo, Miroslav Pajic, Oleg Sokolsky, and Insup Lee, "Attack-Resilient Minimum-Variance Estimation", American Control Conference, (ACC), 2014.
-
Fei Miao, Miroslav Pajic, and George J. Pappas, "Stochastic Game Approach for Replay Attack Detection", 52nd IEEE Conference on Decision and Control (CDC), Florence, Italy 2013.
-
Miroslav Pajic, Oleg Sokolsky, Rajeev Alur, Rahul Mangharam, Nathan Michael, George J. Pappas, Paulo Tabuada, Stephanie Weirich, and Insup Lee, "SPARCS: Synthesis of Platform-aware Attack-Resilient Control Systems", 2nd ACM International Conference on High Confidence Networked Systems (HiCoNS), Philadelphia, PA, 2013.
Reports:
-
Miroslav Pajic, Insup Lee, and George J. Pappas, Attack-Resilient State Estimation for Noisy Dynamical Systems, Technical Report, March 2015.
-
Radoslav Ivanov, Miroslav Pajic, and Insup Lee, Attack-Resilient Sensor Fusion for Safety-Critical Cyber-Physical Systems, Technical Report, September 2014.
Videos:
Attack-resilient Velocity Estimation on a Real Vehicle!
Attack-resilient state estimation on a Generic American Built Car (ABC). We illustrate performance of the proposed attack-resilient state estimator (from the ICCPS'14 paper) when GPS and/or encoder measurements are attacked on a real-vehicle.
Test I - uncut version
Test II - uncut version
Attack-resilient Cruise Control on the LansShark!
Experiments on the Black-I LandShark robot described in the ICCPS'14 paper. We illustrate performance of the proposed attack-resilient state estimator when used for Cruise Control on different surfaces/terrains. During the experiments we activate/deactivate the resilient state estimators, run different attacks on different sensors, save data, change the gains of the PID loop, and trim the vehicles. Trimming was necessary on the LandShark because the two sides of the vehicles are unbalanced and we are not controlling the steering of the vehicle.
Attack-resilient Cruise Control on Tiled Surface
Attack-resilient Cruise Control on Grass
Attack-resilient Cruise Control on Snow!
Attack-resilient Cruise Control on Grass with only a constant attack on the GPS
Additional tests of Attack-resilient Cruise Control on Tiled Surface
Additional tests of Attack-resilient Cruise Control on Grass
Attack-Resilient Fusion for Safety-Critical CPS
This video illustrates performance of the proposed attack-resilient sensor fusion algorithm when each sensor provides a set with all possible values for the true state of the measured variable (described in the paper). We recorded an experiment with the LandShark robot, in which the robot was driven straight and velocity was estimated by three sensors: left and right encoders and GPS. The input speed was set to 0.8 mph initially, before being raised to 1 mph. We introduced a maximal offset attack on the right encoder (see the paper for an explanation of the attack). We compared the performance of the abstract sensor fusion algorithm (with velocity measurements as input) for two communication schedules - Ascending and Descending, and showed that the size of the fusion interval under the Ascending schedule is never larger than that under Descending.